Agents in St. Louis say they have busted up a ring of IT workers using false identities who worked for U.S. companies in order to send the profits back to North Korea.
The FBI says that thousands of North Korean IT workers created false digital identities as Americans in order to perform remote work in the U.S. and raise money for weapons programs in the Democratic People’s Republic of Korea.
Jay Greenberg, special agent in charge of the FBI’s field office in St. Louis, tells the RFT that “thousands upon thousands” of workers in North Korea have been inadvertently employed by companies in the U.S. to perform temporary or contracted IT work. North Korea then takes a portion of their income to fund ballistic and nuclear missile programs.
“More likely than not, if [companies] have augmented their IT workforce, they have employed one of these people and at a bare minimum unknowingly funded North Korean weapons programs,” Greenberg says.
A local victim’s ID was stolen and used to open accounts, and a laptop in the Eastern District of Missouri was accessed by a North Korean IT worker.
The FBI has so far seized $1.5 million in payments that would have gone to the IT workers and subsequently to the North Korean government, according to Greenberg. But that doesn’t foil the whole operation.
“It does not take all the money out of the system, but we know this will be an extreme setback for them,” Greenberg says.
The U.S. considers North Korea an “embargoed country,” so in most circumstances, people or entities in the U.S. are barred from doing business with people in North Korea. Greenberg could not say how many companies or workers are involved, but described the companies as “victims.”
Last year, several media outlets reported on the possibility that American companies could be unknowingly hiring North Korean IT workers. And in many cases, the companies had no idea they were employing malicious cyber actors, Greenberg says. The IT workers often completed the work that was requested from them. Only their identities were fake.
The North Koreans leveraged the increased use of remote work in recent years by creating fake online personas that would have little to no chance of being scrutinized.
The IT workers also hid their identities by accessing “home networks” outside of North Korea through scams that offered unwitting people the opportunity to “earn money at home” by selling access to their wifi system, Greenberg says.
“They’re sort-of remoting into someone’s network and appearing as if they’re working from an IP address in, say, St. Louis,” Greenberg says.
The individuals working on behalf of the North Korean government went so far as to set up fake company websites chock-full of stock photos and claiming to be located in the U.S. One such company was FoxySun Studios LLC. When an FBI agent went to the address in San Francisco listed on FoxySun's website, they found it didn't exist.
In February, the Riverfront Times asked the FBI aboutan application for a search warrant related to this investigation that had been made public in the federal court filing system. The FBI stated that the application for the warrant had been made publicly available by mistake. Both the RFT and the Daily Beast, which had also noticed the errant filing, agreed to withhold publication of any information based on the document until today, so as not to compromise the investigation.
The FBI agent applying for the search warrant identified himself in it as a member of the "cyber squad" working out of the bureau's St. Louis field office. The application was primarily interested in Gmail accounts suspected of being controlled by people working on behalf of North Korea.
"To carry out the freelancing fraud, information technology workers create and utilize a large number of email accounts," the application reads. "They create and use different personas to create freelancer accounts and disguise their identity."
The application for the search warrant, which runs 85 pages, says that Google turned over records from more than 225 Gmail accounts in response to a subpoenas related to the investigation.
The document says that in August 2019, the FBI interviewed an unidentified individual in the U.S. who has an account on Upwork, a freelancing platform that connects businesses to freelance coders and other tech workers. This person told the FBI that he was being paid by another individual to allow that individual to remote into his computers in the United States and procure freelancing gigs via Upwork.
Payments for the work went to a Paypal account controlled by the unidentified individual in the U.S. That person would keep a portion of the money and send the rest along, unaware it was going to individuals affiliated with the North Korean government.
The search warrant application suggests that tech workers earning money for North Korea would go so far as to show up to virtual interviews for freelancing work, though they would not turn on their webcams.
The application for the warrant also indicates that the individuals aiding in the funneling of money to the North Korean government used other platforms in addition to Upwork, including Freelancer, Guru and Fiverr.
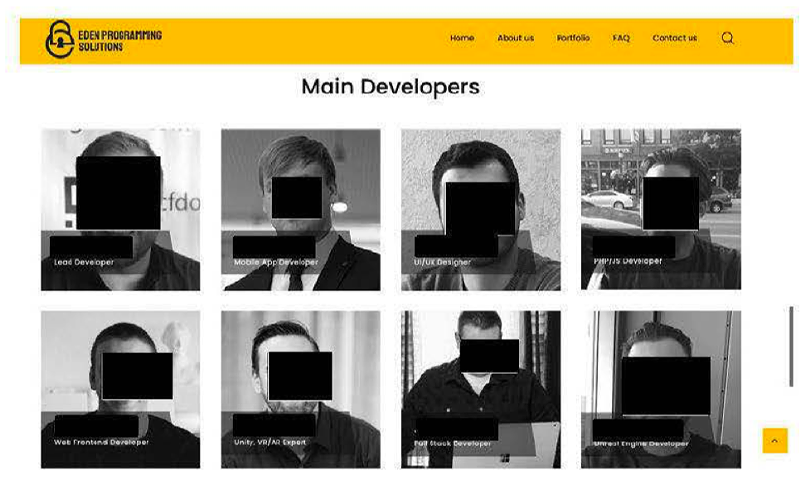
The FBI has seized certain domains used to obtain freelance work under fraudulent identities, including edenprogram.com, which North Korean IT workers used as a software development and portfolio website.
Greenberg encouraged companies who hire outside IT help to scrutinize who they hire and demand video conferences for face-to-face communication.
“They may not look like the driver’s license they submitted,” Greenberg says.
The workers may also have phone numbers with area codes that don’t match the place they say they live in. Or they may give a mailing address that doesn’t match their location.
“A really light internet search will probably reveal inconsistencies that should give them enough reason to dig a little more,” Greenberg says.
Subscribe to Riverfront Times newsletters.
Follow us: Apple News | Google News | NewsBreak | Reddit | Instagram | Facebook | Twitter | Or sign up for our RSS Feed